The 403 Forbidden error is one of the most frustrating HTTP status codes a site owner or developer can encounter. Unlike the more familiar 404 Not Found, which signals that a resource doesn’t exist, the 403 error means the requested resource is there, but the server explicitly denies access to it. This typically indicates a permissions issue, security misconfiguration, or an overly strict access control policy.
While the root cause can vary based on server software, file ownership, CMS (like WordPress), or even security plugins, the outcome is the same: users are blocked, bots are locked out, and services dependent on public availability fail. Understanding why a 403 error appears, how it differs from other HTTP codes, and what steps are necessary for resolution is critical for anyone managing a website. This guide explores the full lifecycle of the 403 error from detection and diagnosis to prevention and best practices.
Understanding HTTP Status Code 403
A 403 error is an HTTP response status code that signifies forbidden access. When a client sends a request to the server, and the server understands the request but refuses to authorize it, it returns a 403. This doesn’t mean the page is missing (like a 404), nor does it require authentication (like a 401). It means the server has made a deliberate decision to block access. Depending on the environment, this restriction may stem from server configuration (e.g., Apache or Nginx), file system permissions, or application-layer security rules. Administrators often configure 403 responses intentionally to protect sensitive directories, restrict bots, or enforce access control layers. Still, misconfiguration or plugin interference can accidentally cause a 403 on legitimate content. Whether you manage a small blog or a large eCommerce platform, knowing how to interpret a 403 response is essential to maintaining uptime and user experience.
What Does 403 Forbidden Mean?
The phrase “403 Forbidden” communicates a precise technical message: “Access to this resource is understood, but not allowed.” From a browser’s point of view, it tried to retrieve a page or asset that exists, but the server denied permission. Unlike server errors (5xx), a 403 is client-facing and signals an intentional barrier. Web developers may configure it via .htaccess, server config files, or firewall rules. In WordPress sites, plugins like security suites or redirect managers can trigger a 403 error unintentionally. Understanding the semantics of this status code is the first step toward resolving it.
How 403 Differs from Other Errors, Like 404 or 401
While these status codes may appear similar, they have distinct meanings and implications. A 404 Not Found suggests the resource doesn't exist. A 401 Unauthorized implies authentication is required and hasn’t been provided. A 403 Forbidden, on the other hand, says: “Even if you are authenticated or the page exists, access is explicitly denied.” This distinction matters when debugging, especially on servers that serve dynamic content or rely on CMS systems like WordPress. Mistaking a 403 for a missing page can mislead your troubleshooting path, wasting time and risking user abandonment. Recognizing the differences ensures you're diagnosing the right problem with the right tools.
Common Causes of a 403 Error
The causes of a 403 error span across infrastructure layers—from file system permissions on Linux servers to web server configuration directives. On Apache, it may be .htaccess denying access; on Nginx, it might be an issue with root path restrictions. A misconfigured security plugin in WordPress can ban users or block resources. A CDN may block access based on firewall rules or geographic restrictions. In all these cases, the user receives a 403 Forbidden page, while the underlying issue may be invisible unless you access logs, server settings, or plugin dashboards. Correctly identifying the source is critical to selecting the right fix and preventing recurrence.
File and Folder Permission Issues
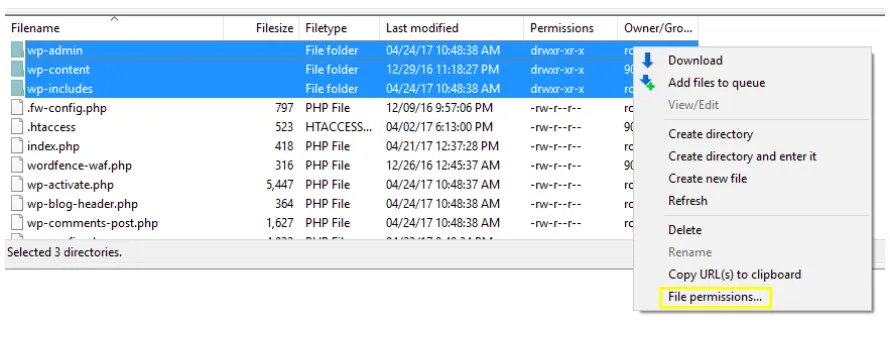
Incorrect file and folder permissions are among the most common triggers of a 403 error. On a Linux-based hosting environment, if file permissions are too restrictive, the server will block access, even if the file itself exists and is correctly linked. Typically, folders should be set to 755 and files to 644. Anything more restrictive (e.g., 600 for files or 700 for folders) may result in a 403. Moreover, the web server user (such as www-data or apache) must have appropriate read and execute access to serve those files.
Hosting environments with misaligned user ownership—often seen during site migrations or file uploads via FTP—can cause silent permission errors. Always verify and, if necessary, reset permissions recursively via SSH or hosting file managers to restore normal behavior.
.htaccess Misconfigurations
The .htaccess file in Apache environments is powerful but dangerous when misused. This file allows granular control over redirects, access rules, file blocking, and directory protection. However, a single bad rule can trigger a 403 site-wide. For example, denying all traffic from a certain IP or folder may inadvertently block admin access. Restrictive rewrite rules, missing directory indexes, or IP restrictions are common culprits. In many WordPress hacks or plugin conflicts, the .htaccess is modified without the admin realizing it. A quick way to test this is to temporarily rename the .htaccess file and see if the 403 disappears.
If so, regenerate it via WordPress permalinks or review it manually for deny directives, malformed syntax, or unsupported directives on your server type.
IP Blocking or Firewall Rules
Many security-conscious admins configure IP allowlists or blacklists using .htaccess, hosting firewalls, or services like Cloudflare. While effective in reducing brute-force attacks or bot traffic, improper IP filtering can lock out legitimate users, or worse, you as the site owner. Some WAFs block IPs based on country, suspicious behavior, or rate-limiting policies. When improperly tuned, these can result in a 403. Check whether your hosting provider has default firewall rules or if plugins like Wordfence are blocking requests from known IPs. Logs are crucial here; analyze them for patterns before making changes. If you use a CDN, also review their firewall logs to ensure you're not being blocked at the edge layer before the request even hits your server.
Invalid Index File or No Directory Listing
Web servers need a default file to load when accessing a folder—typically index.php, index.html, or default.html. If no such file exists and directory listing is disabled (which it should be for security), the server returns a 403. This happens often on new installations, subdirectories, or after removing homepages without configuring a fallback. On Apache, the DirectoryIndex directive controls this behavior. In WordPress, certain themes may rely on specific index files, and deleting or renaming them accidentally triggers the error. Always ensure your directories contain a valid index file or that your web server is configured to redirect appropriately.
Restrictive Server Settings (Apache, Nginx)
Both Apache and Nginx have security modules and default directives that may block content access under certain conditions. For Apache, mod_rewrite, mod_security, or overly strict AllowOverride rules may trigger a 403. For Nginx, errors often arise from incorrect location blocks, permission mismatches between user and root directives, or blocked file types.
Unlike CMS-level issues, these require server-level access to diagnose and fix. Check configuration files like httpd.conf or nginx.conf, and validate syntax before reloading. Restarting the server may be required after making changes. Be cautious: incorrect config tweaks can take your entire site offline. Always back up configuration files before editing.
WordPress, while flexible and powerful, can be particularly sensitive to permission-related issues that result in 403 errors. Since it relies heavily on themes, plugins, and a dynamically generated file structure, even a minor misconfiguration can lead to widespread access denial. Often, these errors aren’t tied to the server alone—they originate from inside WordPress itself.
For example, a plugin update may change rewrite rules, or a new security plugin may block file execution it deems suspicious. Also, WordPress’s reliance on .htaccess and index files makes it more vulnerable to minor changes in these files. In addition, WordPress's complex permission layers—including user roles and file ownership—can exacerbate 403 issues when not managed carefully. Recognizing these CMS-specific triggers is vital for proper diagnosis and rapid restoration of site availability.
Theme or Plugin Conflict
WordPress sites often run dozens of plugins and custom themes. While powerful, this increases the chance of code conflicts, particularly with security or redirect-related functions. A plugin may programmatically add .htaccess rules, redirect logic, or change file permissions without notifying the admin. Similarly, some themes include their own security or caching layers that override server defaults. If a 403 error appears after a recent plugin or theme installation, disable it immediately.
Use SFTP or the hosting file manager to rename the plugin directory if the dashboard is inaccessible. Always test plugin compatibility and avoid overlapping functionalities (e.g., two firewall plugins) that may conflict. Maintaining a staging environment helps identify conflicts before they reach production.
Security Plugins Blocking Access
Popular security plugins like Wordfence, iThemes Security, and All In One WP Security are powerful tools, but their aggressive defaults can sometimes block legitimate access. Features like IP blocking, country restrictions, failed login limits, and file change monitors are effective, but when misconfigured, they generate false positives. You may find yourself locked out of wp-admin or unable to access the homepage because the plugin has flagged your IP or behavior as suspicious. To confirm this, disable the plugin via SFTP by renaming its folder and refreshing the site. If access is restored, check plugin settings or whitelist your IP before reactivating. Logging tools within these plugins can also reveal blocked requests that were erroneously marked as threats.
Incorrect File Ownership
Every file and folder in a WordPress installation must be owned by the correct server user (e.g., www-data, apache, or nginx). If ownership changes—for example, after restoring a backup, migrating between servers, or manually uploading via FTP—the server may deny access, even if file permissions are technically correct. This often causes 403 errors, especially on VPS or dedicated servers. You can check file ownership via SSH using ls -l and change it using chown. For example:
sudo chown -R www-data:www-data /var/www/html
Apply this carefully, and only if you understand Linux file permission structures. Hosting environments like Managed VPS simplify this process with integrated permission repair tools.
Fixing 403 Error on Shared Hosting
Shared hosting environments, while budget-friendly, offer limited access to server-level tools. However, most providers include features like cPanel or DirectAdmin, which allow manual permission changes, plugin management, and .htaccess edits. If you encounter a 403 on shared hosting, first check for incorrect file permissions, especially after bulk file uploads or CMS migrations.
Use the File Manager in cPanel to review folder permissions—public_html, wp-content, and wp-admin should generally be 755. Resetting them recursively can resolve access issues. Additionally, regenerate .htaccess from the WordPress dashboard by visiting Settings → Permalinks and saving changes (if accessible). Disabling plugins via the file manager and checking IP restrictions from security dashboards can also eliminate plugin-related blocks.
Fixing 403 Error on VPS and Dedicated Servers
On VPS and dedicated servers, you have full control over the operating system, web server, and permissions—meaning both the potential and responsibility for resolving 403 errors rest entirely on your configuration. The flexibility of these environments allows for granular debugging and correction using SSH, server logs, and direct config file access. However, they also introduce complexity; a single misconfigured .conf file or restrictive rule in iptables can trigger a 403 across an entire directory. Proper resolution starts with understanding which layer is denying access: web server, file system, or firewall. Use server logs (error and access) to correlate timestamps and understand rejection reasons. Managed environments like Rackset’s VPS hosting often include built-in tools to scan file integrity and restore default permissions securely.
Checking Nginx or Apache Error Logs
Web server logs are your first line of visibility into any access issue. On Apache, check error.log and access.log typically located at /var/log/apache2/ or /usr/local/apache/logs/. On Nginx, use /var/log/nginx/error.log. These files record every access attempt, including its status code, originating IP, and requested URI. If a 403 appears, review the exact time and see what rule or configuration rejected the request. Sometimes, Apache’s mod_security or Nginx’s location blocks produce silent 403s without clearly telling you why. Using tail -f during live access tests is helpful. Knowing what triggered the denial (permissions, config, IP block, or missing file) can save hours of blind debugging.
Adjusting SELinux or ModSecurity
Security modules like SELinux (Security-Enhanced Linux) and ModSecurity offer OS- and application-level protections respectively. However, they are notorious for triggering false positives. On systems with SELinux enabled, file contexts must align with the expected access control policies. Use ls -Z to verify and restorecon or chcon to fix mislabeled files. For ModSecurity, rules can be overly aggressive, especially in shared rule sets like OWASP CRS. Temporarily disabling ModSecurity in Apache or tweaking specific rules based on logs can help restore functionality without fully disabling protection. Always re-enable and tune security modules after resolving the issue.
Restarting the Web Server and Clearing the Cache
Sometimes, a 403 error persists even after fixing permissions or rules due to server caching or a failed reload of updated configurations. Restart your web server using:
sudo systemctl restart apache2
# or
sudo systemctl restart nginx
Also, clear any internal caches, like fastcgi_cache for Nginx or object cache in WordPress (if using Redis or Memcached). In setups with Cloudflare or a CDN, purge the external cache to ensure the 403 isn’t coming from an edge node. Restarting the server reloads the latest configuration and ensures changes to .htaccess, nginx.conf, or firewall settings take effect. On Cloud Hosting, many of these steps can be automated with one-click actions in the control panel.
Using Security Tools and Firewalls Effectively
Firewalls, both at the server and application level, are essential to prevent unauthorized access, but they’re also common sources of 403 errors. WordPress admins often forget that tools like Cloudflare, CSF (ConfigServer Security & Firewall), and plugins like Wordfence can generate access-denied messages if improperly configured. A robust firewall strategy includes clear allowlists for admin IPs, geofencing rules for known attack regions, rate limiting, and real-time threat detection. However, applying such rules without exclusions or context can block legitimate traffic. It’s critical to balance protection with accessibility, especially on public-facing sites.
SSL Certificates and 403 Errors
Though often overlooked, SSL misconfigurations can cause a 403 error, especially when HTTPS is enforced improperly. For example, if a site is configured to redirect all traffic to HTTPS but lacks a valid SSL Certificate, the server may deny access. This is common when switching from HTTP to HTTPS without properly installing a certificate or when using mixed content (loading non-secure assets over HTTPS).
In WordPress, plugins that force SSL or manipulate redirection can exacerbate the problem. Additionally, some servers enforce strict SSL client verification, denying access when certificate chains are broken. It's essential to validate the certificate via your hosting panel or services like SSL Labs. For a deeper comparison between certificate types, refer to our SSL Certificate guide.
Secure Your Website: How to Fix Chrome’s “Not Secure” Warning?
Mismatch in HTTPS Configuration
When a website redirects to HTTPS but the server is not configured to serve HTTPS correctly (or lacks a valid certificate), the result is often a 403 or a browser security warning. This can also occur when the HTTPS flag in WordPress is forced, but the web server is missing the corresponding rewrite rules or 443 port listener. Check your server configuration and ensure it supports HTTPS with the proper certificate. On WordPress, verify that both the “WordPress Address” and “Site Address” use https://.
Forcing HTTPS Without SSL Redirect
In some cases, administrators force SSL redirection through .htaccess or plugins without verifying the certificate status. If users are redirected to a secured version of a page that isn’t properly configured, the server may block the request with a 403. Always validate SSL readiness before enforcing redirection. Managed WordPress Hosting platforms often include automated SSL provisioning and verification, minimizing these risks.
Mixed Content Leading to Forbidden Access
Mixed content refers to loading non-secure (HTTP) resources on a secure (HTTPS) page. Some modern servers or CDNs treat this as a policy violation, particularly when configured with strict security headers. The result can be blocked scripts, fonts, or full pages. Use browser developer tools and scanning plugins to identify mixed content. Solutions include updating asset URLs, using HTTPS-compatible themes, and adjusting Content-Security-Policy headers.
When to Contact Your Hosting Provider
Sometimes, no amount of debugging or rule-tweaking resolves the issue, especially when the 403 stems from host-level restrictions. Shared hosts may enforce rules that restrict access to certain files, directories, or scripts for security. If you’ve ruled out permission, .htaccess, firewall, and plugin causes, reach out to your hosting provider.
What to Ask When Facing Persistent 403s
Be prepared with details: the exact error message, the URL being blocked, steps already taken, and any error logs you can provide. Ask whether your IP is blocked, whether ModSecurity rules are at play, or if there are account-specific restrictions. Clarify if there are limits on file types, memory usage, or directory execution. A proactive support ticket can reduce resolution time dramatically.
Hosting Restrictions and Account-Level Policies
Many shared hosts disable features like directory listing, certain PHP functions, or access to system files. On the other hand, Managed VPS or Cloud Hosting platforms provide you full control, letting you configure access precisely. If 403s are a recurring issue on shared plans, upgrading to a dedicated environment may prevent future headaches.
Preventing 403 Errors in the Future
Prevention is about proactive architecture. Ensure correct permissions (755 for folders, 644 for files), use well-coded plugins and themes, and always test redirects or firewall rules in staging environments before production. Employ automatic file change monitors, maintain up-to-date SSL, and audit .htaccess changes regularly. Leveraging services like WordPress Hosting or Managed VPS provides a scalable infrastructure with proper safeguards baked in.
Use of Security Best Practices
Limit the number of users with admin privileges. Set up Two-Factor Authentication. Avoid using “admin” as a username. Disable XML-RPC if not needed. Add security headers via .htaccess. Secure wp-config.php and disable file editing in the dashboard.
Leveraging Managed Hosting Environments
Providers like Rackset offer hardened, isolated hosting environments with built-in security layers. These include DDoS protection, WAF, automatic SSL management, and resource isolation. Moving to Cloud Hosting or Managed VPS reduces the surface area for misconfigurations and allows full visibility via logs and dashboards.
File Audit and Logging Strategy
Implement routine log reviews—both error and access logs—to catch early anomalies. Use tools like Fail2Ban, Logwatch, or Cloudflare analytics. Track user behavior, plugin changes, and backend modifications. Pair this with version-controlled .htaccess and backup configurations for quick rollback when needed.
Conclusion and Final Checklist for Troubleshooting 403 Error
The 403 Forbidden error is more than a nuisance—it’s often a sign of deeper misconfiguration or overly aggressive security. While it protects resources, it can also block legitimate users or critical processes if not carefully managed. From file permissions and server rules to plugin conflicts and SSL settings, diagnosing a 403 demands a structured, multi-layered approach. Here’s a final checklist:
✅ Check file/folder permissions and ownership
✅ Test disabling .htaccess temporarily
✅ Review plugin and theme conflicts
✅ Analyze firewall/IP block logs
✅ Confirm SSL configuration and redirection behavior
✅ Clear cache layers (server/CDN)
✅ Contact hosting if all else fails
A secure, reliable environment, like that of a Managed VPS or Cloud Hosting, gives you more control and less guesswork.
Tools for Detecting a 403 Error
When trying to diagnose and resolve a 403 Forbidden error, several tools can help you identify the issue quickly and efficiently. These tools allow you to track down the exact cause of the error and help you take the necessary actions to fix it.
Google Search Console
Purpose: One of the best tools for detecting site issues, especially those related to access and HTTP errors, is Google Search Console. It allows you to receive reports about the indexing status of your site and spot any problems related to accessing specific pages.
How to Use It:
Log in to Google Search Console.
Navigate to the "Coverage" section to see a list of pages with any crawling or indexing issues.
If you see a 403 error listed for a specific URL, it means Google couldn't access that page.
For more details, use the "URL Inspection" tool to check the accessibility of specific pages and see why Google was unable to crawl them.
Benefit: This tool is helpful in determining which pages on your site are not accessible to Google and provides insights into why a 403 error occurred on those pages.
Developer Tools (Browser Developer Tools)
Purpose: Developer Tools is a powerful feature available in most modern browsers (like Google Chrome or Firefox). It helps you view HTTP requests and responses, which can assist in identifying a 403 error.
How to Use It:
Open the site where you are experiencing the 403 error.
Press F12 or right-click and select "Inspect" (or "Inspect Element" in some browsers) to open Developer Tools.
Go to the Network tab.
Reload the page, and in the Network tab, you’ll see all the requests made. If any of the requests have a 403 status code, it means access is being denied to that specific resource.
Benefit: Developer Tools give you a clear view of what’s happening behind the scenes. You can see if certain requests are being blocked due to permissions or other configuration issues.
cURL
Purpose: cURL is a command-line tool used to send HTTP requests. It can help you check if a specific URL is accessible and return the HTTP status code (including 403).
How to Use It:
Open your terminal (or Command Prompt).
Enter the following command:
curl -I http://yourwebsite.com/page
This command sends a request to the server and returns the HTTP headers. If you see a 403 response, it means the server is refusing access to that page.
Benefit: cURL is a simple and effective way to check if a page is accessible via the server and what status code is being returned.
Log Files (Server Logs)
Purpose: Most websites maintain log files that track all incoming requests and responses. These logs can be a valuable source of information when trying to pinpoint the cause of a 403 error.
How to Use It:
Access your server's log files, often found in cPanel or through SSH access.
Look for log files like error.log or access.log.
Search the logs for any 403 errors or denied access entries.
Analyze the logs to see if the issue is related to permissions, misconfigurations, or security settings.
Benefit: Server logs provide in-depth information about the requests and why they were blocked. They can help you track down the root cause of the 403 error.
Preventing 403 Errors in the Future
Ensure Proper File Permissions
Use Well-Coded Plugins and Themes
What You Should Do:
Regularly Test Redirects and Firewall Rules in Staging Environments
What You Should Do:
Monitor and Maintain SSL Certificates
What You Should Do:
Implement File Change Monitoring
What You Should Do:
Limit the Number of Admin Users
What You Should Do:
Review and Audit .htaccess Regularly
What You Should Do:
What You Should Do:
Use tools like SecurityHeaders.io to check whether your site has proper security headers configured and to get suggestions for improvements.
How 403 Errors Differ from Other Errors, Like 404 or 401
While 403 Forbidden errors may seem similar to other common HTTP status codes like 404 Not Found or 401 Unauthorized, they are distinct and indicate different issues. Understanding the differences between these errors is crucial for troubleshooting, as it helps you identify the underlying cause more effectively.
403 Forbidden vs 404 Not Found
403 Forbidden:
Meaning: The resource exists, but the server is explicitly denying access to it.
Cause: This error occurs when the server understands the request but refuses to authorize access. It’s a permissions issue. The user might be authenticated or the resource may exist, but the server or security settings prevent access (due to restricted permissions, IP blocking, misconfigurations, etc.).
Example: You have an existing webpage, but access to it is restricted based on security rules or file permissions (for example, admin-only access).
404 Not Found:
Meaning: The resource does not exist on the server.
Cause: A 404 error happens when the server cannot find the requested resource. This could be because the page was deleted, moved, or the URL was mistyped. It does not indicate any problem with permissions, just that the resource is absent.
Example: A user tries to visit a webpage that no longer exists, or they’ve mistyped the URL.
Key Difference: A 403 error indicates that the resource exists, but access is denied (due to permissions or access control settings). A 404 error means the resource is missing entirely, and the server can't find it to serve the request. While a 403 blocks access to something that’s there, a 404 signals that something is not there at all.
403 Forbidden vs 401 Unauthorized
403 Forbidden:
Meaning: The server understands the request but refuses to authorize it. Authentication or credentials may have been provided, but the server still denies access.
Cause: This error typically occurs when the permissions of the resource are not sufficient for the user’s role or when the server intentionally blocks access based on security rules. Even if the user is authenticated, access is explicitly denied.
Example: A logged-in user tries to access a restricted admin area, but their user role doesn’t allow them to view the page.
401 Unauthorized:
Meaning: The request lacks valid authentication credentials, or the credentials provided are incorrect.
Cause: This error occurs when a user tries to access a resource that requires authentication but hasn’t provided the proper credentials or hasn’t logged in. A 401 indicates that the user needs to authenticate before accessing the resource.
Example: A user tries to visit a password-protected page but hasn’t logged in or has used incorrect login credentials.
Key Difference: A 401 error specifically refers to a lack of authentication or incorrect authentication, meaning the user is either not logged in or has provided invalid credentials. A 403 error, however, suggests that the user has been authenticated but does not have permission to access the requested resource due to other factors like roles, permissions, or security restrictions.
403 Forbidden vs 405 Method Not Allowed
403 Forbidden:
Meaning: The server understands the request, but access is blocked due to permissions or server-side rules.
Cause: A 403 occurs because of a permissions issue (e.g., file or directory restrictions, IP blocks, or security settings).
Example: A server may deny access to a file because it’s restricted to certain IPs or user roles.
405 Method Not Allowed:
Meaning: The server recognizes the method used in the request (like GET, POST, DELETE) but does not allow that method for the specified resource.
Cause: This error happens when a client attempts to perform an action that the server does not permit for that particular resource. For example, trying to POST to a URL that only supports GET requests.
Example: Attempting to submit a form using a POST method to a page that only allows GET requests.
Key Difference: A 403 error is related to access control, meaning access to a resource is blocked even if the method is correct. A 405 error indicates that the method (GET, POST, DELETE) used in the request is not allowed for that specific resource, regardless of whether the resource is accessible.
403 Forbidden vs 500 Internal Server Error
403 Forbidden:
Meaning: The server understands the request, but access to the resource is denied due to permission issues.
Cause: This is typically caused by security or permission configurations that deliberately block access, such as firewall settings, misconfigured plugins, or server-level restrictions.
Example: A server rejects access to a page because the .htaccess file is blocking it.
500 Internal Server Error:
Meaning: The server encountered an unexpected error and couldn’t complete the request.
Cause: This error often signals issues with server configuration, server overload, or script errors, which are not related to permissions or access control.
Example: A PHP script on the server crashes or there’s a misconfiguration in server settings like Apache or Nginx.
Key Difference: A 500 error indicates an internal server error where something went wrong on the server's side, while a 403 error indicates that the server deliberately denied access to the resource, usually because of permission settings or security rules.
Summary of Differences:
403 Forbidden means access is denied to an existing resource, often due to permissions or security settings.
404 Not Found indicates that the resource doesn’t exist on the server.
401 Unauthorized means authentication is missing or invalid, requiring login credentials.
405 Method Not Allowed refers to an unsupported HTTP method for a given resource.
500 Internal Server Error is an unexpected server issue, usually unrelated to permissions.

Leave a Reply